It is said that personal data protection in software development should be handled by cybersecurity experts. Senior developers do care about their code protection against SQL-injections, XSS and other threats. But security is not only about these threats, it is more complex. Security is about some actions that should be taken by every employee, even by office manager.

Everyone MUST care about the security!
In the first part of this article we describe common security points using concrete examples which are not directly related to programming. This article is based on my talk dedicated to cybersecurity “Secure your application data with Symfony” on Symfony London 2017.
You may assume that a hack is when hackers crack your passwords, break into operating systems, try to find a vulnerability in your application. In practice there are much simpler ways how to steal the information.
Sitting in the conference hall among developers (people who usually take security more seriously than average users) I noticed that they lost their sense of awareness. My neighbor to the right entered his login and password for Asana (that was used in his company for task management). I might easily record his fingertips movement by my phone and use the data to gain access to his account. Meh, no hacking is necessary; plain carelessness could lead to a serious data leakage. Moreover, I could get considerably much data than needed using social engineering technique.

Real photos from Symfony London 2017. These people were working with secret information and did not care about the workaround.
As you can see on these photos (truly authentic, made by my colleagues) not only my neighbor had that particular problem.
Why should we care?
One of the first questions you may ask is “Why should we give a damn about security? What is the probability the application I develop will be hacked?” The answer to this apparently simple question is not that straightforward. If you develop something like a landing page for a small company you might not care at all. However there are industries like FinTech, MedTech, EdTech, etc., where a single PII (Personally identifiable information) leakage may ruin the whole project. Each industry is based on users’ trust. This trust shatters if, for example, bank transaction data leaks.
There is no such thing as unimportant PII. Any personal data must be protected.
Some PII may seem genuinely non threatening yet giving access to much more sensible information. For instance, SSN, Social Security Number, gives access to vast amount of data ranging from medical to financial.
Who must take care about the security?
It is not possible to assign only one employee in the company “to be responsible for the security”. Everyone must care about the security starting from CTO/CIO down to an office manager. What can be easier than breaking into assistant’s account using fishing and collect classified information by asking standard questions?
Security must be every company employee’s concern.
In my practice, there were cases when the application was hard to hack thanks to proper protection. In contrast it was quite easy to break into the customer’s CEO mailbox which was connected to 90% of all services. Indeed, this risk can be mitigated by proper behavior, but the fact itself must encourage us to change our mindset.
Everyone should care about the security, even office manager. CONSTANT VIGILANCE!
Onion security model
It is impossible to make a 100% protected application. There is always a backdoor which hackers may use. Our goal, as developers, is to make their work as hard as we can. We create obstacles which could be very simple at first level: secure passwords, access restrictions and so on. On the second level go more complex approaches such as two-factor authentication and resources access control. Further goes the next security wall and so on.
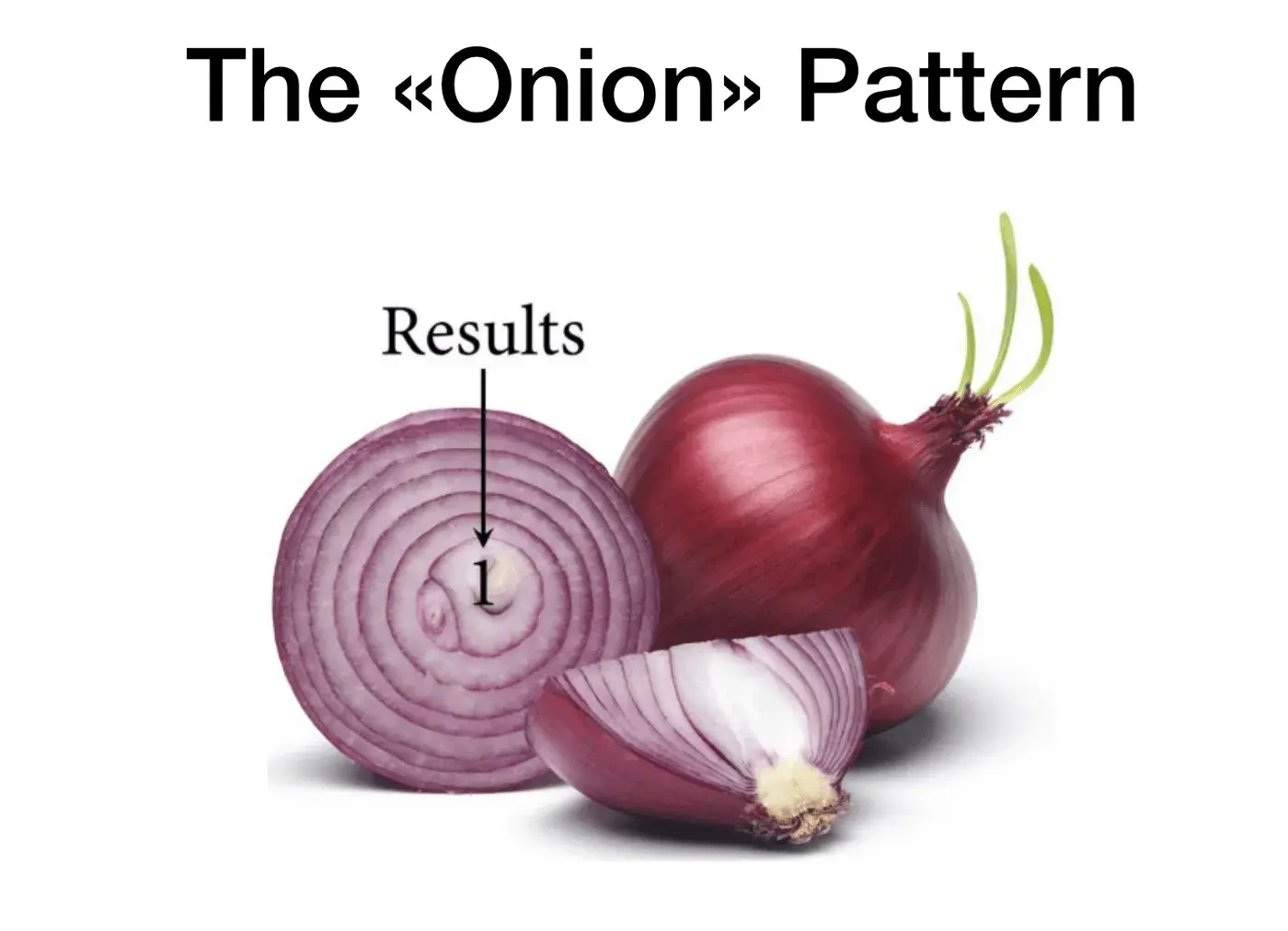
Security arrangement looks like an onion: a hacker broken through one security barrier meets the next one. This arrangement greatly helps in security planning: it is unnecessary to elaborate an ideal model, one may think through just the next level, then another one, then even more. As a result the hack can require exhaustive amount of time while your employees can get alerts on suspicious activity and act in timely manner.
Types of protection
Basically there are three components of protection:
- Physical — access to workplaces where PII is handled is physically restricted;
- Administrative — rules and procedures for employees in various situations
- Technological — software and data protection methods
Each component is as crucial as the next one. What can be simpler than losing a laptop with information of vital importance?
Physical protection

The easiest way to hack you is simply to steal your laptop or mobile phone.
Physical intrusion is often undervalued. Modern data storage devices are so small so they can be stolen almost effortless. It concerns not only laptops but also phones which we sometimes lose. These hints will help to reduce risk a bit:
- Always block your phone or laptop. Never leave it unlocked even at your workplace when you are not around.
- Encrypt data on all devices. Nobody has immunity against theft or losing. Even if you have a password protection on your laptop one can extract your unencrypted data smoothly. It is important to enable data encryption on every device you have. Use please a secure password for this encryption.
- Watch workaround. When you are in a public place where are people and cameras around never work with personal information, never enter passwords, etc. Always think about the worst scenario.
Administrative protection
Many developers and IT-experts dislike formal procedures and bureaucracy which interfere with their work by their opinion. Nevertheless, these procedures are to protect them first. Imagine for a moment that an application you develop(ed) is hacked. What will you do? Do you have a clear plan? Do you know how to act step by step? Ask your colleague, boss, CTO, CIO and compare their answers. Do they match?
They will not match with great deal of confidence. This takes us to the point where we must create at least the simplest instruction possible. Such instruction must include the following:
- Immediate reporting. It is the most important thing to inform persons in charge: your boss, CTO, CIO, CEO, system administrator, even if the problem is only suspected. Do not try to deal with the problem yourself but spend 15–30 seconds of your time to share the information. People in charge must be informed to take necessary measures to help you to solve the problem.
- Data protection. If the leakage is going on in the real time, one must have means to terminate data access, possibly even for everyone, including hackers. PII protection must be first.
- Client awareness & clear communication. An open recognition of a problem by you is much better than a message from hackers or in media. Honest and open statement on how much data was leaked, measures taken, apologies made in the right place at the right time may not only save your reputation but even improve it.
- Retrospective. It is important to find where the leakage was initiated and to make a protocol which mitigates the issue. It is not proactive, though, but it will protect against problem recurring.
These are the administrative protection essentials. In the next article we will discuss security techniques which can make your application protected: working with passwords, vault data storage, encryption, data obfuscation and many more.

Constant Vigilance! — that’s the favorite phrase by Alastor Moody, a famous Auror (policeman) in Harry Potter’s world.
Constant vigilance!
